This article was originally posted on VOA and translated by OKN Correspondent.
In addition to the Reconnaissance General Bureau (RGB), which is known for having a cyber hacking program in North Korea, an American cybersecurity company is reporting that the United Front Department (UFD) and the Ministry of State Security also have programs. Analysts say that the North Korean regime is engaged in various and flexible cyber hacking activities as needed. Kim Young-kyo reports.
American cybersecurity company Mandiant reports that other governmental organizations have been engaged in cyber hacking in addition to the RGB, which mainly conducts external intelligence activities for the North Korean regime.
Mandiant also said that the North Korean regime has the flexibility and resilience to create new cyber units as needed, adding that overlapping technologies, strategies, and malicious software are shared resources amongst these operations.
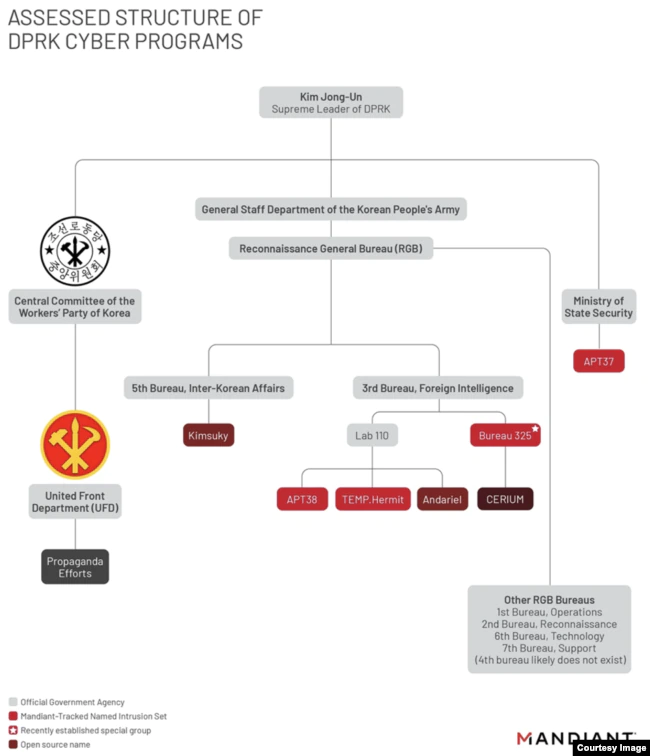
According to the report, the United Front Department focuses on targeting South Korea and spreading information in favor of the North Korean regime.
They have an “army of cyber trolls” to promote pro-North Korean narratives on web forums targeting South Korea.
The report stated that these “cyber trolls” have hacked the IDS of South Korean online users or posted 68,000 North Korean propaganda items with the ultimate goal of establishing pro-North Korean organizations in South Korea.
In the case of the Ministry of State Security (MSS), they independently engage in espionage and counterintelligence operations within the North Korean regime and analyzed the activities of the North Korean hacking group “APT37,” which has been conducting hacking operations since 2012, aligns with the MSS.
The report states that, in the past, APT37 has targeted foreign joint venture partners, North Korean defectors and defector support groups, and humanitarian organizations, but it seems that due to recent similar attacks by another hacking group “Kimsuky,” they assume APT37’s role has been shifted to Kimsuky or the two groups have integrated.
They also report that Kimsuky is under the 5th Bureau of the RGB, which is responsible for inter-Korean affairs.
According to the report, other major hacking groups are managed by the 3rd Bureau (Foreign Intelligence) of the RGB, including Lab 110, TEMP.Hermit, APT38, Andariel, and Bureau 325.
Among them, Lab 110 has been working in northeastern China under the name of a joint venture or trading company, while TEMP.Hermit targets government, defense, telecommunications, and financial institutions around the world since 2013, and is usually referred to as the “Lazarus Group.”
Andariel mainly targets foreign military and government personnel but also engages in criminal activities to generate additional profits for the North Korean regime, and Bureau 325, which came to be known publicly in January 2021, reportedly focuses on gathering information related to COVID-19.
The report assessed that Bureau 325 is suspected of drafting individuals from several other hacking groups in North Korea.
They also mention that over time, they’re seeing a shift from “strictly COVID-19” efforts to targeting defectors, governments, media, cryptocurrency, and financial institutions by [Bureau 325] and that their role within the North Korean regime’s cyber operations is to be growing.
To read the original article in Korean, please click here.


